Telehack: May the Command Line Live Forever
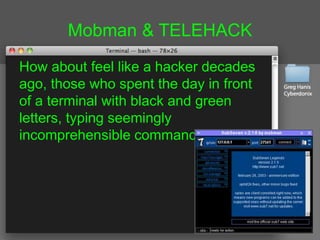
- 1. Mobman & TELEHACK How about feel like a hacker decades ago, those who spent the day in front of a terminal with black and green letters, typing seemingly incomprehensible commands?
- 2. what is telehack |what use is it| • Connect to over 24,000 simulated hosts, with logged-in ghost users with historically-accurate names culled from UUCP network maps. • Hacking metagames, using simplified wardialers and rootkit tools. • User classes that act as an achievements system. • Group chat with relay, and one-on-one chat with send or talk. • Reconstructed Usenet archives, including the Wiseman collection. • A BASIC interpreter with historical programs from the SIMTEL archives. • Standalone playable games, including Rogue and a Z- code interpreter for text adventure games like Adventure and Zork. • Hidden hosts and programs, discoverable only by hacking Telehack itself.
- 6. Basic & Misc Files Filename Description bambi.exe The Adventures of BAMBI animation beer.exe Animation of a jug full with beer cartwhee.exe Animation of a stick-figure doing a cartwheel cartwheel.exe Animation of a stick-figure doing a cartwheel dont-wor.exe Animation of an individual getting shot at firework.exe Animation of a firework fireworks.exe Animation of a firework fishy2.exe Animation about Shamus, the fish glass.exe No information yet globe.exe Animation of the Earth spinning juanspla.exe No information available yet joshua.exe Animation of a text jumble.exe Animation of a text monkey.exe A monkey showing you both middle fingers nasa.exe Animation displaying the N.A.S.A. logo outerlim.exe Animation of a 'television set' being controlled paradise.exe Animation about a destruction of an island prey.exe Animation of a Klingon starship firing a torpedo snowing.exe Animation of Christmas holiday wishes startrek.exe An animation between the NCC-1701 A and D tetris.exe A character based Tetris game trek.exe Animation of the Enterprise taking revenge on the RCA ttest.exe VT100 torture test application turkey.exe Animation of a turkey entering and exiting an oven twilight.exe No information available yet valentin.exe A love message from Dave to Beth wineglas.exe Animation of a glass getting filled with wine xmas.exe Animation of a tree and a toy train
- 7. your computer hard drive memory etc
- 8. Exploring the Telehack network • finger - lists the registered users on the host • finger - lists information about the user • finger @host - lists the users of a particular host • netstat - lists the hosts with which you can connect • ping - checks if the host is active • traceroute - checks the route between you and the destination host • Uupath • Uumap • uuplot
- 10. uupath | uumap
- 11. uuplot gets it’s own slide
- 12. how to connect to other servers • Porthack • rlogin • Wardial • Dial • ftp • telnet
- 14. System tools Filename Description ftpd.exe TEL/OS FTP Daemon ghostports.exe Advertise Decoy Open Host Ports inspect.exe Remote TEL/OS Process Table Inspector iptun.exe L2TP over PPP Daemon killproc.exe Network process killer listuser.exe List Static Core for Any User netlog.exe Remote syslog notification osprober.exe Sniff Remote OS Vendor pdebug.exe Process debugger porthack.exe Probe for Exploitable Host Ports portblock.exe Block Open Port Host Access ptyhide.exe Cloaking Module for PTYCON Line 27 rootkit.exe Rootkit Exploit Launcher satan.exe Security Analyzer over Dial-up wardial.exe AC/Prefix Modem Dialing Prober xmodem.exe XMODEM/CRC support kit
- 15. Account Creation Exploits Filename Description aixacct.exe AIX Account Creation Exploit attacct.exe ATT Account Creation Exploit auxacct.exe AUX Account Creation Exploit bsdacct.exe BSD Account Creation Exploit dynixacct.exe Dynix Account Creation Exploit hp-uxacct.exe HP-UX Account Creation Exploit ibmacct.exe IBM Account Creation Exploit machacct.exe MACH Account Creation Exploit milacct.exe MIL Account Creation Exploit sunosacct.exe SunOS Account Creation Exploit sysvacct.exe SysV Account Creation Exploit ultrixacct.exe Ultrix Account Creation Exploit vmsacct.exe VMS Account Creation Exploit xenixacct.exe Xenix Account Creation Exploit
- 16. Rootkits Filename Description aixkit.exe Support Process for AIX Rootkit attkit.exe Support Process for ATT Rootkit auxkit.exe Support Process for AUX Rootkit bsdkit.exe Support Process for BSD Rootkit dynixkit.exe Support Process for Dynix Rootkit hp-uxkit.exe Support Process for HP-UX Rootkit ibmkit.exe Support Process for IBM Rootkit machkit.exe Support Process for MACH Rootkit milkit.exe Support Process for MIL Rootkit sunoskit.exe Support Process for SunOS Rootkit sysvkit.exe Support Process for SysV Rootkit ultrixkit.exe Support Process for Ultrix Rootkit vmskit.exe Support Process for VMS Rootkit xenixkit.exe Support Process for Xenix Rootkit
- 17. BADGES • ACCT Registered User • ACKNAK Flowing Bytes • 2600HZCaptain Crunch • BABYLON First Dynasty • BRUTE May the FORCE be with you • CBBS Ward & Randy • CLONER Send in the Cloner • CONSEC ConSec Inc • DEPSECDEF Head of the Heads
- 18. • Root refers to the "root" account on Unix and Linux systems. It comes from the idea of directory "trees", the rootGot Root? • being the most basic level of the tree from which all other branches grow. A root user would have access to everything."Getting root" on a system refers to the act of getting admin access. • Rootkits exist in real life, and often do more than just give the user root access. Many involve infesting malware into the system files. Real rootkits are srs bsns. (Actually, they are.) • In Telehack, you must have and run two separate .exe files to get root on a server. These two files must be on the host's file library. The first is an operating-system-specific rootkit, also called a "support process". For example, aixkit.exe, sunoskit.exe, etc. The second is rootkit.exe which will work on all OSs. You must use both files to gain root. • These files are placed, individually, on various servers throughout the telehack network. Some may even be on BBSs. They should be on the same servers for everyone, though this author has noticed some inconsistencies. • After finding the .exes, you must download it, then transfer it to the host you wish to root. • In order to get root, no one else can have root on a system. The OS must match your rootkit. First run the OS-specific rootkit. If it succeeds, then run rootkit.exe. Now you have root and can run more commands than most other people.
- 21. BBS • WTF IS IT? • HISTORY • Inside Telehack
- 22. In order to get root, no one else can have root on that server. If someone else has root, run ps and notice they have at least one process running. You must kill all their other processes (if there is only a support process running, you will be able to root the system with only rootkit.exe.), then the rootkit, to remove their root access. This is done by using kill process .exes that are hidden around the servers, just like the rootkits were. (this sentence should be pointed atKILLPROC.exe and
- 24. tips and tricks • settings up fast connections • LOCK OUT USERS • VARIOUS PROGRAMS • CENTRAL KEY SERVERS
- 25. FUCK PETE I was banned because I took (4!!) roots from 2 top players and they didn't like the competition. Truthfully, I found the game to be fun and reminiscent. I really wanted to play - but if my IP gets banned just because some players find me 'annoying' (read: competitive), then it's no longer a game..it's a clubhouse. I'd be happy to come back and play - in fact, I enjoyed playing very much - but I just thought I'd share the mentality with EVERYONE. ---relay chat--- • (something from egroj about me taking some of his roots) • grice: heh • echo: he stole two of my roots, then egroj stole them from the twit • echo: this new user, funnyman, pisses me off, to be honest... • bigrice: do tell • pete: three votes • ..... • (IP banned)
- 26. DEMO -- Questions • Wanna play a game? • Lets demo this shit!!! • How long till I get banned??? • BETS? • Fuck you pete once again • Incased you missed the first FU PETE
Editor's Notes
- TeleHack is the most interesting game I've played in the last year... a game that most users won't realize is a game at all. The Telehack server runs on real hardware. The operating system is CentOS Linux. The data is being stored in yum (absinthe), while the whole game works based on a single-process epoll driven event loop, written in Perl. It also has a Z-code interpreter, a BASIC interpreter, some Linux syscall stuff for the networking, and a webserver with xmlhttp support for the webclient. The text data has been copied from textfiles.com — an interactive pastiche of 1980s computer history, tying together public archives of Usenet newsgroups, BBS textfiles, software archives, and historical computer networks into a multiplayer adventure game. Yes, this is very cool! Telehack.com is so incredibly fun! If you're familiar with a command line, but not exactly inclined to the finer points of buffer overruns and loopjacking, then telehack.com really delivers an experience like no other game you've ever played. It's like a retro MMO about the culture of hackers in the late 80's and early 90's, when the digital frontier was still an open range, and a mystery to explore. Also, telehack.com includes an amazing breadth of information for those inclined to look at this from an archaeological perspective. The data that span the world of telehack's nearly 25,000 virtual servers represent, what seems to be, an unprecedented and seemingly objective representation of The Internet as it existed prior to the advent of the World Wide Web. The entire project was engineered by "Forbin," an anonymous Silicon Valley engineer whom I seen on a few times, not very talkative though My suggestion: Throw on Spotify, dig up the Hackers soundtrack, and prepare to plunder the ports of old :)
- how to connect, register, login Although you can explore the home environment of the game without registering it is important to create an account for your user. That way, you will get your score recorded and may contact other people who are connected to the game. To do this, type the newuser command in the terminal, and then press Enter. Then simply enter the username (username) and password (password). Once you finish the account creation process, you are automatically logged in to the system. What indicates success in login is the shell prompt, passing point (.) To sign (@). When you want to finish the match, type the exit command or, then press the Ctrl + D keys To access the game again and continue where you left off, just to authenticate the login command.After pressing Enter, the system will require user name and password for the player to proceed.
- The most useful program on the list is the help. When you run it, you have access to a list of other commands available on your terminal. Next to each item is a brief description that explains what the command does and how it can be used. Among the tools available are some indispensable for the player to commit "virtual crimes" such asping, finger, telnet, traceroute, hosts and ipaddr. But there are also many inutilitários as rain - which simulates raindrops on the screen - and starwars, which runs a version of ASCII Art of the great success of George Lucas.
- These executable files are merely for entertaintment purposes only, but are not limited for usage on the target server, but can be loaded into the static core as well.
- Computers on the ARPANet each had a local table of other hosts they could connect with. This table is accessed using thenetstat command. Enter this and a list of computers appears. These belong to corporations and universities, just like they did back in the day.
- ARPANET: A diagram of the ARPAnet as it stood in 1977. By the mid-1980s it had tens of thousands of hosts. Things were so much simpler back then
- Moving between machines can be dull, but there's more to Telehack than that. On the Telehack server, enter the commandquest. You're given the task of finding a host out of the 24,000 that exist within the Telehack universe. The target host will contain a file giving you further instructions. These include entering secret commands and system calls that will increase your status and control over the Telehack universe. Along the way, you'll pass through computers with more executables to map, files full of information and other stuff you can use. Completing quests also gives you bragging rights over other users.
- A host or server in Telehack is an independent node on the network. Most hosts are connected to other hosts, presumably via the early internet. However, there are groups of hosts connected only to each other and not to the rest of the network. Likewise, many BBSs are disconnected from the rest of the network, and can only be accessed by dialup. For the most part, when this Wiki refers to a host or server, we're not talking about a BBS. Hosts are run on many different OSs, including: --- Each OS is not particularly important, except that rootkits and other exploits are tailored for a specific OS.
- These tools are designated for specific administrative tasks on the target systems. These applications are OS independant, and shall be run from the core memory.
- The following "Account Creation Exploit" files can be used to create an account on a remote machine even if no telnet connection can be established (i.e. portblock is running). They have to be executed on the same OS (i.e. to use AIXacct.exe you have to run it from an AIX-based host).
- These kits are necessary to be run before the actual rookit, since every OS has it's own specific programming. Rootkit.exe is an executable program which allows a user to gain root access, or systems privileges, on a host. It is one of the fpur basic tools available to all users in the Telehack lobby. Before it can be run on a host, you must transfer it to the host with FTP. Enter RUN ROOTKIT on any host to gain root. In order to use rootkit.exe, the necessary support process must already be running on the host. For example, to root a SunOS system, you must first run sunoskit.exe. Only one user may obtain root on any given host, but you can oust another user by stopping their processes (seekillproc).
- FINDING FILES ETC>>> MOVING FTP ETC..
- A BBS means a Bulletin Board system. A BBS allows users to connect to it by dialing to it. In the past this was the only way, but with the advent of the internet you can also connect to a BBS by using a hostname. --A BBS is a computer system running software which allows users to download software and read files stored on the system. A BBS was a mini social network of the olden times. People could play games talk with each other and also as a plus download software. While most BBS's were free some used to ask for payment. The BBS is controlled by a system operator(sysop for short). --COMMANDS < f >Files AreaYou can download files from here and also see the size of the files.< w >Who's OnlineSee the list of users connected to the BBS.< j >Tell a jokeOutputs a joke. < y >Yell for SysopPages Sysop, use if the BBS is malfunctioning.< x >Exit To CP/MExits to the OS where additional commands are available.< l >List filesLists the files. You can only list files here, to download use < f >.< q >Quit/log offQuits the BBS and returns you to where you were last.< ? >HelpLists the available commands.
- Stealing Root from Someone Else Keeping RootEdit In order to remove you from a server, a would-be hacker must kill all your other processes, then kill your rootkit. Therefore, it would follow you should try to get as many processes running as possible. It is also rumored that there are .exes designed to mask or hide your existing processes. (This sentence needs to point atPTYHIDE; the application hiding the commands executed from the system monitor on telehack)
- Point out phone number…..
