Disruptive INFOSEC vendor landscape (SOAR focused)
•
3 likes•3,586 views
Disruptive INFOSEC vendor landscape for 2016/2017. Special focus has been given to SOAR and related technologies: - enrich data intake (network traffic analysis NTA and endpoint tooling) - better breach detection toolset (behaviour based detection, sandboxing, endpoint EDR) - new SOAR tooling (data analytics, big data, incident response automation) - solutions with cloud focus (CASB, etc.) or built and run in the cloud (MSSP)
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
More Related Content
Recently uploaded
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Featured
Featured (20)
Product Design Trends in 2024 | Teenage Engineerings

Product Design Trends in 2024 | Teenage Engineerings
How Race, Age and Gender Shape Attitudes Towards Mental Health

How Race, Age and Gender Shape Attitudes Towards Mental Health
AI Trends in Creative Operations 2024 by Artwork Flow.pdf

AI Trends in Creative Operations 2024 by Artwork Flow.pdf
Content Methodology: A Best Practices Report (Webinar)

Content Methodology: A Best Practices Report (Webinar)
How to Prepare For a Successful Job Search for 2024

How to Prepare For a Successful Job Search for 2024
Social Media Marketing Trends 2024 // The Global Indie Insights

Social Media Marketing Trends 2024 // The Global Indie Insights
Trends In Paid Search: Navigating The Digital Landscape In 2024

Trends In Paid Search: Navigating The Digital Landscape In 2024
5 Public speaking tips from TED - Visualized summary

5 Public speaking tips from TED - Visualized summary
Google's Just Not That Into You: Understanding Core Updates & Search Intent

Google's Just Not That Into You: Understanding Core Updates & Search Intent
The six step guide to practical project management

The six step guide to practical project management
Beginners Guide to TikTok for Search - Rachel Pearson - We are Tilt __ Bright...

Beginners Guide to TikTok for Search - Rachel Pearson - We are Tilt __ Bright...
Disruptive INFOSEC vendor landscape (SOAR focused)
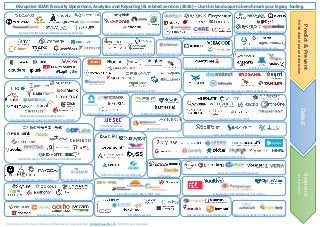
- 1. Network Traffic Analysis (NTA) & Anomaly detection LOG , SIEM and Big Data Platforms Threat Protection for SaaS Vulnerability Assess. (VA) Config audits and Compliance Tokenization, DLP, Monitoring, Encryption DLP for the Cloud IDaaS and CASB - Cloud Access Security Broker Backup into the Cloud Encryption and Key Management Machine Data Analytics & Big Data / Security Operations, Analytics and Reporting (SOAR) Micro Segmentation of Docker ContainersApp Segmentation & Hardening Threat Intelligence Platforms (TIPS) Endpoint Detection & Response (EDR) & Malware Hunting Data Analytics and Visualization Cloud based CDN, DDoS, WAF, ADC IoT Security Cyber Situational Awareness Deception Based Detection Risk Intelligence (IRMS) & prioritization OT/SCADA Security Security Automation and DevOps Incident Response Orchestration and Automation & Situational Awareness User and Entity Behavior Analytics (UEBA/UBA) Endpoint Protection (EPP) Sandbox Analysis MSSP Content Security Web and Mail Threat Intelligence Automation and Sharing Code Testing Predict&Prevent Enrichdatainputanddetection DetectRespond andprotect Comments or corrections? Please send feedback to Philipp Wächter - philipp@waechter.ch - MSSP Product Developer Content Disarm & Reconstruction CDR Offensive Security Mobile Device Security Integrity Based Assurance and Detection Exfiltration detection, DLP IAG – Identity and Access Governance Disruptive SOAR (Security Operations, Analytics and Reporting) & related vendors (2016) – Use this landscape to benchmark your legacy Tooling.
