Spectrum of privacy 2017 01-10
•Download as PPTX, PDF•
0 likes•2,433 views
This document discusses privacy and metadata in online communications. It presents a spectrum of privacy for different types of personal information, from most private like passwords to least private like public information. It then introduces some privacy-forward services like Crypt.info that aim to provide secure messaging without metadata. Crypt.info is described as the "anti-email" that allows anonymous and encrypted communication without identifying information about senders or receivers.
Report
Share
Report
Share
Recommended
Simplifying Social Data: How to Measure and Maximize Your Results on Social M...

Simplifying Social Data: How to Measure and Maximize Your Results on Social M...DesignBloggersConference
Recommended
Simplifying Social Data: How to Measure and Maximize Your Results on Social M...

Simplifying Social Data: How to Measure and Maximize Your Results on Social M...DesignBloggersConference
State of Ad Fraud Ad Blocking Q1 2016 Update Augustine Fou

State of Ad Fraud Ad Blocking Q1 2016 Update Augustine FouDr. Augustine Fou - Independent Ad Fraud Researcher
Dr. Augustine Fou - The Lowdown on Ad Fraud for Advertisers - Seattle Interac...

Dr. Augustine Fou - The Lowdown on Ad Fraud for Advertisers - Seattle Interac...Seattle Interactive Conference
Context of Fraud in Digital Advertising Ecosystem

Context of Fraud in Digital Advertising EcosystemDr. Augustine Fou - Independent Ad Fraud Researcher
Bots Can Do Everything You Can Research by Augustine Fou

Bots Can Do Everything You Can Research by Augustine FouDr. Augustine Fou - Independent Ad Fraud Researcher
State of Digital Ad Fraud Q1 2015 Update by Augustine Fou

State of Digital Ad Fraud Q1 2015 Update by Augustine FouDr. Augustine Fou - Independent Ad Fraud Researcher
More Related Content
Viewers also liked
State of Ad Fraud Ad Blocking Q1 2016 Update Augustine Fou

State of Ad Fraud Ad Blocking Q1 2016 Update Augustine FouDr. Augustine Fou - Independent Ad Fraud Researcher
Dr. Augustine Fou - The Lowdown on Ad Fraud for Advertisers - Seattle Interac...

Dr. Augustine Fou - The Lowdown on Ad Fraud for Advertisers - Seattle Interac...Seattle Interactive Conference
Context of Fraud in Digital Advertising Ecosystem

Context of Fraud in Digital Advertising EcosystemDr. Augustine Fou - Independent Ad Fraud Researcher
Bots Can Do Everything You Can Research by Augustine Fou

Bots Can Do Everything You Can Research by Augustine FouDr. Augustine Fou - Independent Ad Fraud Researcher
State of Digital Ad Fraud Q1 2015 Update by Augustine Fou

State of Digital Ad Fraud Q1 2015 Update by Augustine FouDr. Augustine Fou - Independent Ad Fraud Researcher
Viewers also liked (8)
State of Ad Fraud Ad Blocking Q1 2016 Update Augustine Fou

State of Ad Fraud Ad Blocking Q1 2016 Update Augustine Fou
Dr. Augustine Fou - The Lowdown on Ad Fraud for Advertisers - Seattle Interac...

Dr. Augustine Fou - The Lowdown on Ad Fraud for Advertisers - Seattle Interac...
Bots Can Do Everything You Can Research by Augustine Fou

Bots Can Do Everything You Can Research by Augustine Fou
State of Digital Ad Fraud Q1 2015 Update by Augustine Fou

State of Digital Ad Fraud Q1 2015 Update by Augustine Fou
Similar to Spectrum of privacy 2017 01-10
Similar to Spectrum of privacy 2017 01-10 (20)
DBAs - Is Your Company’s Personal and Sensitive Data Safe?

DBAs - Is Your Company’s Personal and Sensitive Data Safe?
Office 365 security concerns, EU General Data Protection Regulation (GDPR) 

Office 365 security concerns, EU General Data Protection Regulation (GDPR)
3 analytic strategies shree dandekar dell 12-10-13

3 analytic strategies shree dandekar dell 12-10-13
3 analytic strategies shree dandekar dell 12-10-13

3 analytic strategies shree dandekar dell 12-10-13
3 analytic strategies shree dandekar dell 12-10-13

3 analytic strategies shree dandekar dell 12-10-13
Introduction to Predictive Analytics for Marketers: Takeaway version with des...

Introduction to Predictive Analytics for Marketers: Takeaway version with des...
SRV423 [new launch] Introducing Amazon Macie — Visibility and Security for yo...![SRV423 [new launch] Introducing Amazon Macie — Visibility and Security for yo...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SRV423 [new launch] Introducing Amazon Macie — Visibility and Security for yo...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SRV423 [new launch] Introducing Amazon Macie — Visibility and Security for yo...
Password and Account Management Strategies - April 2019

Password and Account Management Strategies - April 2019
Winning the war on data breaches in a changing data landscape

Winning the war on data breaches in a changing data landscape
More from Dr. Augustine Fou - Independent Ad Fraud Researcher
Alternative to ANA's end to end supply chain transparency study v final

Alternative to ANA's end to end supply chain transparency study v finalDr. Augustine Fou - Independent Ad Fraud Researcher
Impact of Loss of 3P Cookies on Publishers' Ad Revenue

Impact of Loss of 3P Cookies on Publishers' Ad RevenueDr. Augustine Fou - Independent Ad Fraud Researcher
Checking abnormal referrer traffic in google analytics

Checking abnormal referrer traffic in google analyticsDr. Augustine Fou - Independent Ad Fraud Researcher
Four types of digital ad spend updated august 2020

Four types of digital ad spend updated august 2020Dr. Augustine Fou - Independent Ad Fraud Researcher
FouAnalytics DIY site media analytics fraud detection baked in

FouAnalytics DIY site media analytics fraud detection baked inDr. Augustine Fou - Independent Ad Fraud Researcher
More from Dr. Augustine Fou - Independent Ad Fraud Researcher (20)
Alternative to ANA's end to end supply chain transparency study v final

Alternative to ANA's end to end supply chain transparency study v final
Impact of Loss of 3P Cookies on Publishers' Ad Revenue

Impact of Loss of 3P Cookies on Publishers' Ad Revenue
Checking abnormal referrer traffic in google analytics

Checking abnormal referrer traffic in google analytics
Four types of digital ad spend updated august 2020

Four types of digital ad spend updated august 2020
FouAnalytics DIY site media analytics fraud detection baked in

FouAnalytics DIY site media analytics fraud detection baked in
Recently uploaded
Recently uploaded (9)
IP addressing and IPv6, presented by Paul Wilson at IETF 119

IP addressing and IPv6, presented by Paul Wilson at IETF 119
SCM Symposium PPT Format Customer loyalty is predi

SCM Symposium PPT Format Customer loyalty is predi
Cybersecurity Threats and Cybersecurity Best Practices

Cybersecurity Threats and Cybersecurity Best Practices
Company Snapshot Theme for Business by Slidesgo.pptx

Company Snapshot Theme for Business by Slidesgo.pptx
Spectrum of privacy 2017 01-10
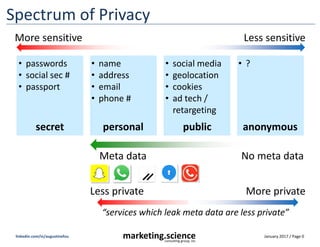
- 1. January 2017 / Page 0marketing.scienceconsulting group, inc. linkedin.com/in/augustinefou Spectrum of Privacy Less private More sensitive More private Less sensitive secret personal public anonymous • passwords • social sec # • passport • name • address • email • phone # • social media • geolocation • cookies • ad tech / retargeting • ? Meta data No meta data “services which leak meta data are less private”
- 2. January 2017 / Page 1marketing.scienceconsulting group, inc. linkedin.com/in/augustinefou Set of Privacy-Forward Services crpt.info pass.wd netw.rk • secure messaging • no meta data • strong passwords • easy to use for humans • device-to- device comms • atomic permissions No meta data brow.sr • session based keys • perfect forward privacy meta data Key problem to solve: weak passwords single private key d2d comms + + Meta data Phone # and email used to identify endpoints reveal identity and meta data. • ownership • permissions to spend ++ mon.ey undemo- cratic
- 3. crpt.info 1. anything you want tracked and saved for later, use EMAIL 2. anything you do not want tracked, with no meta data about the transmission, use crpt.info “the anti-email” consumer alpha currently available at http://crpt.info
- 4. January 2017 / Page 3marketing.scienceconsulting group, inc. linkedin.com/in/augustinefou personal mail lockbox only you have private key for decrypting messages dropped into your lock box public phone senders use a public phone to anonymously create and send messages to your lock box Offline Analogies – no meta data
- 5. January 2017 / Page 4marketing.scienceconsulting group, inc. linkedin.com/in/augustinefou 1. No meta data (no phone # or email required) 2. Endpoints are anonymous, not associatable 3. Message encrypted with recipient’s public key 4. Every part of transmission is “transient” ? ?njbf8nw8cw9casssddnasda3131wcwyfkj01 Public key encryption Private key decryption Top Features
