Report
Share
More Related Content
Viewers also liked
Viewers also liked (20)
Introduction to pointers and memory management in C

Introduction to pointers and memory management in C
Reversing & Malware Analysis Training Part 4 - Assembly Programming Basics

Reversing & Malware Analysis Training Part 4 - Assembly Programming Basics
More from Farid Diah
More from Farid Diah (10)
PErisian Sumber Terbuka vs. Perisian Sumber Tertutup

PErisian Sumber Terbuka vs. Perisian Sumber Tertutup
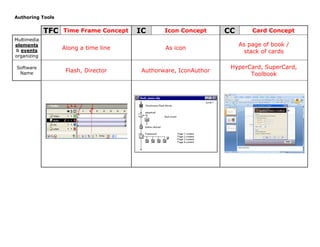
Authoring tools worksheet
- 1. Authoring Tools<br />TFCTime Frame ConceptICIcon ConceptCCCard ConceptMultimedia elements & events organizingAlong a time lineAs iconAs page of book / stack of cardsSoftware NameFlash, DirectorAuthorware, IconAuthorHyperCard, SuperCard, Toolbook<br />
