Like it or not, you're already in the cloud
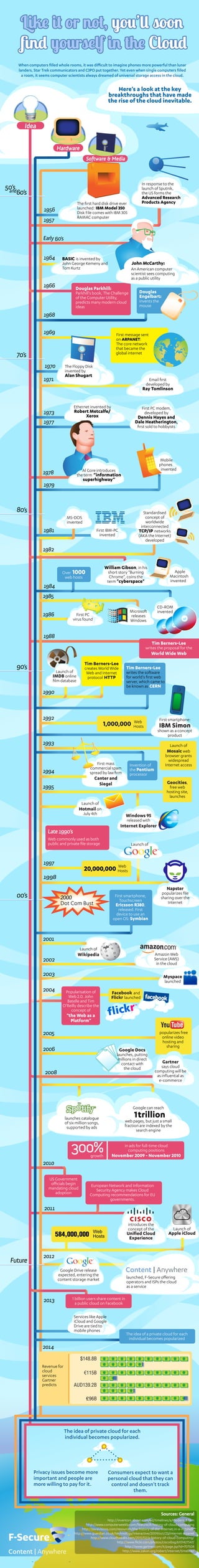
- 1. When computers filled whole rooms, it was difficult to imagine phones more powerful than lunar landers, Star Trek communicators and C3PO put together. Yet even when single computers filled a room, it seems computer scientists always dreamed of universal storage access in the cloud. Here’s a look at the key breakthroughs that have made the rise of the cloud inevitable. Idea Hardware Software & Media In response to the 50’s and60’s launch of Sputnik, the US forms the Advanced Research The first hard disk drive ever Products Agency 1956 launched: IBM Model 350 Disk File comes with IBM 305 RAMAC computer 1957 Early 60’s 1964 BASIC is invented by John George Kemeny and John McCarthy: Tom Kurtz An American computer scientist sees computing as a public utility 1966 Douglas Parkhill: Parkhill's book, The Challenge Douglas of the Computer Utility, Engelbart: predicts many modern cloud invents the ideas mouse 1968 1969 First message sent on ARPANET: The core network that became the 70’s global internet 1970 The Floppy Disk invented by Alan Shugart 1971 Email first developed by Ray Tomlinson Ethernet invented by First PC modem, 1973 Robert Metcalfe/ developed by Xerox Dennis Hayes and 1977 Dale Heatherington, first sold to hobbyists Mobile phones Al Gore introduces invented 1978 the term “information superhighway” 1979 80’s Standardised MS-DOS concept of invented worldwide interconnected 1981 First IBM-PC TCP/IP networks invented (AKA the Internet) developed 1982 William Gibson, in his Over 1000 short story “Burning Apple web hosts Chrome”, coins the Macintosh term "cyberspace" invented 1984 1985 CD-ROM Microsoft invented 1986 First PC releases virus found Windows 1988 Tim Berners-Lee writes the proposal for the World Wide Web Tim Berners-Lee 90’s creates World Wide Tim Berners-Lee Launch of Web and Internet writes the software IMDB online protocol HTTP for world's first web film database server, which came to be known as CERN 1990 1992 First smartphone: Web 1,000,000 Hosts IBM Simon shown as a concept product 1993 Launch of Mosaic web browser grants widespread First mass Invention of Internet access commercial spam the Pentium 1994 spread by law firm processor Canter and Siegel Geocities, 1995 free web hosting site, launches Launch of Hotmail on July 4th Windows 95 released with Internet Explorer Late 1990’s Web commonly used as both public and private file storage Launch of 1997 Web 20,000,000 Hosts 1998 Napster popularizes file 00’s 2000 First smartphone, sharing over the Touchscreen Dot Com Bust Ericsson R380, Internet released. First device to use an open OS: Symbian 2001 Launch of Wikipedia Amazon Web 2002 Service (AWS) in the cloud 2003 Myspace launched 2004 Popularisation of Facebook and Web 2.0. John Flickr launched Batelle and Tim O’Reilly describe the concept of "the Web as a Platform" 2005 popularizes free online video hosting and sharing 2006 Google Docs launches, putting millions in direct contact with Gartner the cloud says cloud 2008 computing will be as influential as e-commerce Google can reach launches catalogue 1 trillion of six million songs, web pages, but just a small supported by ads fraction are indexed by the search engine 300% growth in ads for full-time cloud computing positions November 2009 - November 2010 2010 US Government officials begin European Network and Information mandating cloud Security Agency makes Cloud adoption Computing recommendations for EU governments. 2011 introduces the concept of the Launch of Web 584,000,000 Hosts Unified Cloud Experience Apple iCloud 2012 Future Google Drive release expected, entering the content storage market launched, F-Secure offering operators and ISPs the cloud as a service 2013 1 billion users share content in a public cloud on Facebook Services like Apple iCloud and Google Drive are tied to mobile phones The idea of a private cloud for each individual becomes popularized 2014 $148.8B Revenue for cloud €115B services Gartner predicts AUD139.2B ₤96B The idea of private cloud for each individual becomes popularized. Privacy issues become more Consumers expect to want a important and people are personal cloud that they can more willing to pay for it. control and doesn’t track them. Sources: General http://inventors.about.com/od/timelines/a/modern_5.htm http://www.computerweekly.com/feature/A-history-of-cloud-computing http://sixrevisions.com/resources/the-history-of-the-internet-in-a-nutshell/ http://www.guardian.co.uk/technology/interactive/2009/oct/23/internet-arpanet http://www.cloudtweaks.com/2011/02/a-history-of-cloud-computing/ http://www.flickr.com/photos/ciscoibsg/6101427547/ http://www.gartner.com/it/page.jsp?id=707508 Content | Anywhere http://www.zakon.org/robert/internet/timeline/ http://www.f-secure.com/content-anywhere
