Report
Share
More Related Content
What's hot
What's hot (20)
Minimum mode and Maximum mode Configuration in 8086

Minimum mode and Maximum mode Configuration in 8086
Viewers also liked
Viewers also liked (20)
Direct Memory Access (DMA)-Working and Implementation

Direct Memory Access (DMA)-Working and Implementation
Similar to Dma transfer
Similar to Dma transfer (20)
I/O Interfaces: Bridging the Digital and Physical Worlds

I/O Interfaces: Bridging the Digital and Physical Worlds
Recently uploaded
Recently uploaded (20)
Transcript: New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024
Unleashing Real-time Insights with ClickHouse_ Navigating the Landscape in 20...

Unleashing Real-time Insights with ClickHouse_ Navigating the Landscape in 20...
Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx

Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx
Time Series Foundation Models - current state and future directions

Time Series Foundation Models - current state and future directions
Emixa Mendix Meetup 11 April 2024 about Mendix Native development

Emixa Mendix Meetup 11 April 2024 about Mendix Native development
Scale your database traffic with Read & Write split using MySQL Router

Scale your database traffic with Read & Write split using MySQL Router
The Future Roadmap for the Composable Data Stack - Wes McKinney - Data Counci...

The Future Roadmap for the Composable Data Stack - Wes McKinney - Data Counci...
Microsoft 365 Copilot: How to boost your productivity with AI – Part one: Ado...

Microsoft 365 Copilot: How to boost your productivity with AI – Part one: Ado...
Zeshan Sattar- Assessing the skill requirements and industry expectations for...

Zeshan Sattar- Assessing the skill requirements and industry expectations for...
New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024

New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024
Potential of AI (Generative AI) in Business: Learnings and Insights

Potential of AI (Generative AI) in Business: Learnings and Insights
Varsha Sewlal- Cyber Attacks on Critical Critical Infrastructure

Varsha Sewlal- Cyber Attacks on Critical Critical Infrastructure
Generative AI - Gitex v1Generative AI - Gitex v1.pptx

Generative AI - Gitex v1Generative AI - Gitex v1.pptx
The Ultimate Guide to Choosing WordPress Pros and Cons

The Ultimate Guide to Choosing WordPress Pros and Cons
Genislab builds better products and faster go-to-market with Lean project man...

Genislab builds better products and faster go-to-market with Lean project man...
React Native vs Ionic - The Best Mobile App Framework

React Native vs Ionic - The Best Mobile App Framework
Generative Artificial Intelligence: How generative AI works.pdf

Generative Artificial Intelligence: How generative AI works.pdf
The Role of FIDO in a Cyber Secure Netherlands: FIDO Paris Seminar.pptx

The Role of FIDO in a Cyber Secure Netherlands: FIDO Paris Seminar.pptx
Use of FIDO in the Payments and Identity Landscape: FIDO Paris Seminar.pptx

Use of FIDO in the Payments and Identity Landscape: FIDO Paris Seminar.pptx
Dma transfer
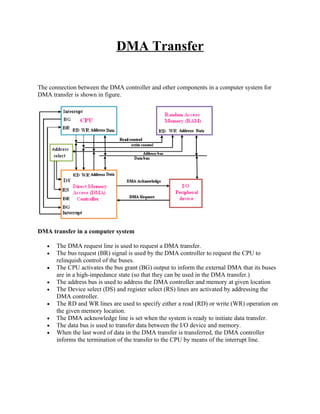
- 1. DMA Transfer The connection between the DMA controller and other components in a computer system for DMA transfer is shown in figure. DMA transfer in a computer system • The DMA request line is used to request a DMA transfer. • The bus request (BR) signal is used by the DMA controller to request the CPU to relinquish control of the buses. • The CPU activates the bus grant (BG) output to inform the external DMA that its buses are in a high-impedance state (so that they can be used in the DMA transfer.) • The address bus is used to address the DMA controller and memory at given location • The Device select (DS) and register select (RS) lines are activated by addressing the DMA controller. • The RD and WR lines are used to specify either a read (RD) or write (WR) operation on the given memory location. • The DMA acknowledge line is set when the system is ready to initiate data transfer. • The data bus is used to transfer data between the I/O device and memory. • When the last word of data in the DMA transfer is transferred, the DMA controller informs the termination of the transfer to the CPU by means of the interrupt line.