Analog Transmission Techniques
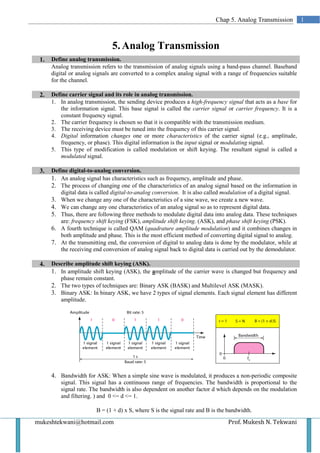
- 1. Chap 5. Analog Transmission 1 5. Analog Transmission 1. Define analog transmission. Analog transmission refers to the transmission of analog signals using a band-pass channel. Baseband digital or analog signals are converted to a complex analog signal with a range of frequencies suitable for the channel. 2. Define carrier signal and its role in analog transmission. 1. In analog transmission, the sending device produces a high-frequency signal that acts as a base for the information signal. This base signal is called the carrier signal or carrier frequency. It is a constant frequency signal. 2. The carrier frequency is chosen so that it is compatible with the transmission medium. 3. The receiving device must be tuned into the frequency of this carrier signal. 4. Digital information changes one or more characteristics of the carrier signal (e.g., amplitude, frequency, or phase). This digital information is the input signal or modulating signal. 5. This type of modification is called modulation or shift keying. The resultant signal is called a modulated signal. 3. Define digital-to-analog conversion. 1. An analog signal has characteristics such as frequency, amplitude and phase. 2. The process of changing one of the characteristics of an analog signal based on the information in digital data is called digital-to-analog conversion. It is also called modulation of a digital signal. 3. When we change any one of the characteristics of a sine wave, we create a new wave. 4. We can change any one characteristics of an analog signal so as to represent digital data. 5. Thus, there are following three methods to modulate digital data into analog data. These techniques are: frequency shift keying (FSK), amplitude shift keying. (ASK), and phase shift keying (PSK). 6. A fourth technique is called QAM (quadrature amplitude modulation) and it combines changes in both amplitude and phase. This is the most efficient method of converting digital signal to analog. 7. At the transmitting end, the conversion of digital to analog data is done by the modulator, while at the receiving end conversion of analog signal back to digital data is carried out by the demodulator. 4. Describe amplitude shift keying (ASK). 1. In amplitude shift keying (ASK), the amplitude of the carrier wave is changed but frequency and phase remain constant. 2. The two types of techniques are: Binary ASK (BASK) and Multilevel ASK (MASK). 3. Binary ASK: In binary ASK, we have 2 types of signal elements. Each signal element has different amplitude. 4. Bandwidth for ASK: When a simple sine wave is modulated, it produces a non-periodic composite signal. This signal has a continuous range of frequencies. The bandwidth is proportional to the signal rate. The bandwidth is also dependent on another factor d which depends on the modulation and filtering. ) and 0 <= d <= 1. B = (1 + d) x S, where S is the signal rate and B is the bandwidth. mukeshtekwani@hotmail.com Prof. Mukesh N. Tekwani
- 2. 2 Analog Transmission Minimum bandwidth is obtained when d = 0 or B = S and maximum bandwidth is obtained when d = 1 and B = 2S. 5. From the diagram we observe that the middle of the bandwidth coincides with the carrier frequency fc. So if we have a bandpass channel available we can choose fc so that the modulated signal occupies the bandwidth. 6. Consider a digital signal with a high voltage of 1V and a low voltage of 0 V. We multiply the digital signal by the carrier signal. When the amplitude of the digital signal is 1, the amplitude of the carrier frequency is max and when the amplitude of the digital signal becomes 0, the amplitude of the carrier signal is also 0. 7. In full-duplex transmission, data has to be sent in both directions. The available bandwidth is divided into two with 2 carrier frequencies. The total bandwidth of 100 kHz is divided into 2 parts of 50 kHz each. The available bandwidth for each direction is now 50 kHz. Multilevel ASK: In multilevel ASK, there are more than 2 levels of the digital signal. We can use 4, 8, 16 or more different amplitudes for the signal and modulate the data using 2, 3, 4 or more bits at a time. 5. Describe frequency shift keying (FSK). 1. In FSK, the frequency of the carrier is changed to represent the binary 1 and 0. For binary 0 the carrier frequency will be f1 and for binary 1, the frequency will be f 2. 2. The frequency of the modulated signal is constant for the duration of one signal element (say binary 0) but changes for the next signal element (say binary 1). 3. The peak amplitude and phase remain constant. 4. Bandwidth for FSK: The middle of one bandwidth is f1 while the middle of the other bandwidth is f2. These two bandwidths are Δf apart from the midpoint between the two bands. The difference between the two frequencies is 2 Δf. Multilevel FSK: This is also called multiple FSK. More than 2 frequencies are used. E.g., we can use 4 different frequencies to send 2 bits at a time. To send 3 bits at a time, we use 8 frequencies. Prof. Mukesh N Tekwani mukeshtekwani@hotmail.com
- 3. Chap 5: Analog Transmission 3 6. Describe phase shift keying (PSK). In phase shift keying, the phase of the carrier is changed to represent different signal elements (1 / 0). The peak amplitude and frequency remain constant. Binary PSK: 1. There are only 2 signal elements one with a phase shift of 0o ; the other with a phase shift of 180 o. 2. The advantage of PSK is that it is less susceptible (or affected) by noise. In PSK, the bit detection depends on the phase of the carrier signal. Although noise can change the amplitude of the carrier, changes in phase are more difficult. Also, PSK is superior to FSK because we donot require 2 carrier signals. 3. Implementing FSK is simple because the signal element with phase 180o is just the complement of the signal element with phase 0. We multiply a polar NRZ data signal with a carrier signal. We represent the 1 bit (positive voltage) by phase starting at 0 . The 0 bit (negative voltage) is represented by a phase starting at 1800 Quadrature PSK: 1. Instead of using only 2 variations of a signal, we use four variations. 2. Each phase shift represents 2 bits. A phase of 00 now represents 00; 900 represents 01; 1800 represents 10; and 2700 represents 11. This technique is called 4-PSK or Q-PSK. The pair of bits represented by each phase is called a dibit. 3. The incoming bits are first passed through a serial to parallel converter. It sends one bit to a modulator and the next bit to another modulator. 4. The 2 signals created by multipliers are sine waves with same frequency but different phases. When these two signals are added, the result is another sine wave which can have phases of 45o, - 45o, 135o, or -135o. Since there are four kinds of signal elements in the output signal, we can send 2 bits per signal element. mukeshtekwani@hotmail.com Prof. Mukesh N. Tekwani
- 4. 4 Analog Transmission 7. Describe Quadrature Amplitude Modulation (QAM). 1. This modulation technique is a combination of ASK and PSK. 2. In QAM technique, we change two characteristics – the amplitude of one carrier wave and the and the phase of the other carrier wave. 3. The amplitude of the two carrier signals are different. 8. Define analog-to-analog conversion. 1. Analog-to-analog conversion I the representation of analog information by an analog signal. 2. Such a modulation is required if the medium is bandpass. 3. Analog-to-analog conversion is achieved in 3 ways: Amplitude Modulation (AM), Frequency Modulation (FM), and Phase Modulation (PM) 9. Describe Amplitude Modulation (AM) 1. Modulation is defined as the process of combining an input signal and a carrier frequency to produce a signal whose bandwidth is centered around fc. 2. In AM, we use two signals: the carrier signal and the modulating signal. Both are analog signals. 3. The carrier signal is modulated so that its amplitude varies with changes in the amplitude of the modulating signal. 4. The frequency and phase of the carrier signal remain constant, only the amplitude changes. 5. The modulating signal is the envelope of the carrier wave. 6. The bandwidth of the AM signal is two times the bandwidth of the modulating signal. The central frequency is fc. The signal components above and below fc carry the same information. Why is modulation of analog signal necessary? Modulation of an analog signal is necessary for two reasons: a) A higher frequency may be needed for transmission of a signal. The size of the antenna decreases as the carrier frequency increases so a modulated signal is needed. b) Modulation permits frequency division multiplexing. 10. Describe Frequency Modulation (FM) 1. In Frequency Modulation, the frequency of the carrier wave is changed to follow the changing amplitude of the modulating signal. 2. The peak amplitude and phase of the carrier signal remain constant but as the amplitude of the modulating (or information) signal changes, the frequency o the carrier signal also changes. 3. The total bandwidth of the FM signal is given by: BW = 2(1 + β)B, where β is the modulation index Prof. Mukesh N Tekwani mukeshtekwani@hotmail.com
- 5. Chap 5: Analog Transmission 5 11. Discuss Phase Modulation (PM). 1. In Phase Modulation, the phase of the carrier signal is changed in accordance with the changing amplitude of the modulating signal. 2. The peak amplitude and frequency of the carrier signal remain constant, but the phase of the carrier changes with changes in amplitude of the information signal (or the modulating signal). mukeshtekwani@hotmail.com Prof. Mukesh N. Tekwani
