Securely Access Networks Anywhere with VPN
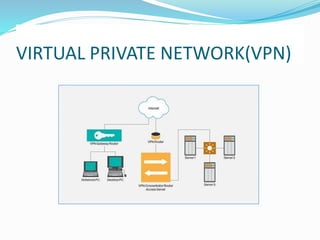
- 2. ABOUT VPN A virtual private network (VPN) is a technology that creates a safe and encrypted connection over a less secure network, such as the internet. VPN technology was developed as a way to allow remote users and branch offices to securely access corporate applications and other resources. To ensure safety, data travels through secure tunnels and VPN users must use authentication methods -- including passwords, tokens and other unique identification methods -- to gain access to the VPN.
- 3. TYPES OF VPN There are two basic types of VPN- Remote Access VPN- It allows a user to connect to a private network and avail its services and resources securely. The connection between the user and the private network happens through the internet and the connection is secure and private. It is useful for business as well as home users. Site to Site VPN- It is also called as router-to-router VPN and is mostly used in corporate businesses. Companies, located at different geographical locations connect to the network of one office location to the network of another
- 4. office location. When networks of the multiple offices of the same company are connected using site-to-site VPN, it is called as intranet based VPN. When companies use site-to-site VPN to connect to the office of different company, it is called as extranet based VPN. Basically, a site-to-site VPN creates a virtual bridge between the networks at geographically distant offices and connects them through the internet and maintain a secure and private communication between the networks.
- 5. TYPES OF VPN PROTOCOLS Internet Protocol Security or IPSec- Internet Protocol Security or IPSec is used to secure Internet communication across an IP network. IPSec secures Internet Protocol communication by authenticating the session and encrypts each data packet during the connection. IPSec operates in two modes, Transport mode and Tunneling mode, to protect data transfer between two different networks. The transport mode encrypts the message in the data packet and the tunneling mode encrypts the entire data packet. IPSec can also be used with other security protocols to enhance the security system.
- 6. Layer 2 Tunneling Protocol (L2TP):L2TP or Layer 2 Tunneling Protocol is a tunneling protocol that is usually combined with another VPN security protocol like IPSec to create a highly secure VPN connection. L2TP creates a tunnel between two L2TP connection points and IPSec protocol encrypts the data and handles secure communication between the tunnel. Point – to – Point Tunneling Protocol (PPTP): PPTP or Point-to-Point Tunneling Protocol creates a tunnel and encapsulates the data packet. It uses a Point-to-Point Protocol (PPP) to encrypt the data between the connection. PPTP is one of the most widely used VPN protocol and has been in use since the time of Windows 95. Apart from Windows, PPTP is also supported on Mac and Linux.
- 7. ADVANTAGES OF VPN • Enriched Security- When you connect to a network like the VPN, the data is kept secured and encrypted. In this way, the information is kept away from the hacker’s eyes. • Remote Control- In case of a company, the advantage of having a VPN is that the information can be accessed even from home or any other place. That’s why VPN can increase productivity within a company. • Share files- A VPN service can be used if you have a
- 8. group that needs to share data for an extended period. • Online Anonymity- Through a VPN you can browse the web in complete anonymity. Compared to hide IP software or web proxies, the advantage of a VPN service is that it allows access to both web applications and websites in complete anonymity. • Unblock websites and bypass filters- VPNs are great for accessing blocked websites or for bypassing internet filters. That is why there is an increased number of VPN services used in countries where internet censorship is applied.
- 9. Change IP address- If you need an IP address from another country, the VPN can provide it. Better performance- Bandwidth and efficiency of the network can generally be increased once a VPN solution is implemented. Reduce Costs- Once a VPN network is created, the maintenance cost is very low. More than that, if you opt for a service provider, the network setup and surveillance is no more a concern.
- 11. DISADVANTAGES OF VPN Performance Issues- If you are using a VPN service, it may create a problem while taking to the website one wants to get access. The VPN service connects the user to a private network. Some Virtual Private Networks might take a longer time to load the website which is to be accessed. This is the most common disadvantage which may be seen in using a VPN service. Matter of legality- The use of Virtual Private Networks (VPNs) may not be legal in a country. Local organizations and companies may face the problems of censorship to a particular website. This is mainly due to the absence of direct control over the Internet while
- 12. Using a VPN. So a reliability of a VPN comes under question. However, it is not illegal in India as there is not any specific law regarding VPN. VPN might intrude in one’s online activity and use his data- Some VPN providers might ask for data in exchange of service. There is no complete protection of your online browsing as it can be tracked by the VPN service providers. Even though a VPN can hide the real IP address and remove internet restrictions, but there is no security of one’s online browsing. So the care must be taken while using a free or a low cost VPN.
- 13. Difficulty in its Set-Up:- It might not be very difficult for Individual users to use a VPN service which can simply be achieved by downloading it in the form of any app or software. But companies may find it difficult to set-up a virtual private network over their premises which may , in result, bring complexity to their network connections and affect each device used in the companies. Add more costs- VPN is a premium service which is not available free. If one wants to use a VPN router, he will also need an additional router hardware with it. There are a lot of private connections but they are generally not reliable and have lots of limitations.
- 14. VPNs in India How does an Indian VPN work? If you are living in India and plan to travel to any part of the world, you can connect back to your home network. You can connect back to home with your family and friends. This means that if you are an Indian living in any part of the world, can securely and privately get access to internet. Some of the frequently used VPNs in India are- ExpressVPN NordVPN
- 15. PrivateVPN IPVanish ProtonVPN The above mentioned VPNs in India provide more than a thousand servers and locations with respective average speeds, allow torrents and number of connections at the same time with supported systems like MacOS, Windows, Android, iOs and windows Phone. So VPNs
- 16. Case Law Internet Service Providers vs. UOI (2005):- " We observed that though VPN is being defined and discussed by both the parties, on access through Internet as well as on direct leased line. The Respondent mentioned that the VPN provided on direct leased line by ISPs is not allowed. This stand of the DOT we accept because by basic definition of ISP, it has to be only Internet based activity. License of ISP permits them the activity concerned with access of Internet and use of its content for IT enabled services. As rightly contended by DOT, VPN was not allowed as a part of ISP license, it is fair for us, therefore, to hold that it becomes a separate service. The quantum of entry fee and revenue share to be charged for a separate service from the service provider would require the recommendations of TRAI as per Sec 11 (1)(a)(i)(ii) of TRAI Act.”
- 17. Thank you SONALIKA SINGH B.A.L.L.B DIV- B ROLL NO. 59